Blog
July 24, 2020
JMeter Regular Expression Extractor: How to Extract Tokens and Session IDs to Variables
Open Source Automation
What is the JMeter Regular Expression Extractor? And how do you use it? Find out in this blog.
Let’s get started.
What Is the JMeter Regular Expression Extractor?
Back to topThe JMeter Regular Expression Extractor is used for extracting information from responses. It is helpful in particular for extracting tokens and session IDs.
Why Use the JMeter Regular Expression Extractor?
You should use the JMeter Regular Expression Extractor when tokens and session IDs are sent in the request header. With the Regular Expression Extractor, you can easily work with tokens and session IDs as variables.
Tokens and session IDs are sent in the request header. Sometimes, when scripting in Apache JMeter™, we need to work with them as variables. For example, in cases where the following requests use these session IDs or tokens in their parameters (in POST requests for example). So, we need to find a way to do this easily in JMeter. This post will review how to do this with the JMeter Regular Expression Extractor.
Experience how BlazeMeter helps teams do JMeter testing at enterprise scale. Try BlazeMeter for free today >>
Back to topHow to Use the JMeter Regular Expression Extractor
Locating the Token
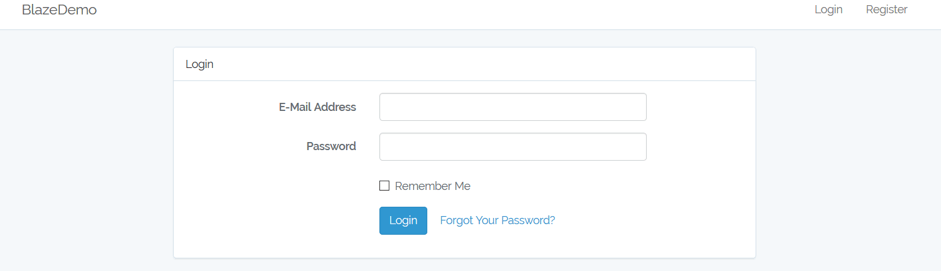
Let’s use as an example login action of the BlazeDemo website (Make sure you register, and also check the “Remember Me” option to login successfully).
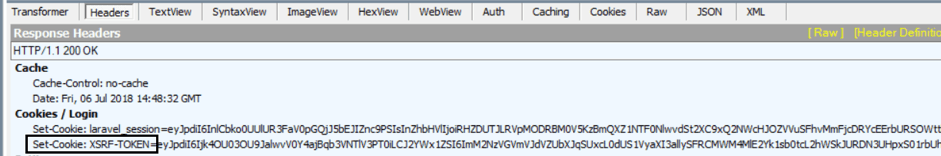
If we look into the traffic communication between the client (our browser) and the endpoint or server (Blazedemo.com) we can see there is a token given into the header of the response, as a cookie field.
If you are wondering what I’m using to see this information, well, I’m using Fiddler, but you can also see this using Charles, or the Network tab of the Developer Tool of your browser.
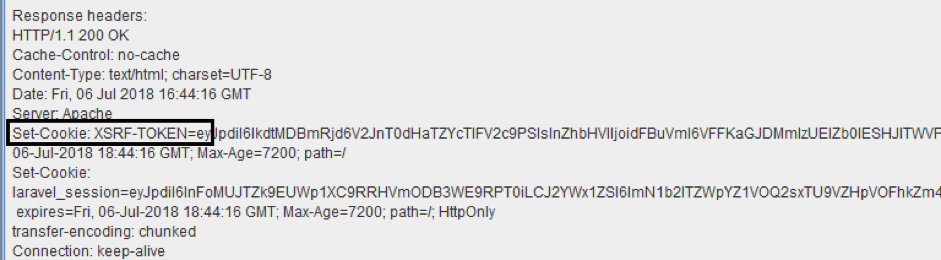
As you can see, this is a XSRF token.
Locating the Token in Your JMeter Script
So now, lets create a JMeter script for the Login step. To do this you can use the BlazeMeter recorder (a free Chrome plugin).
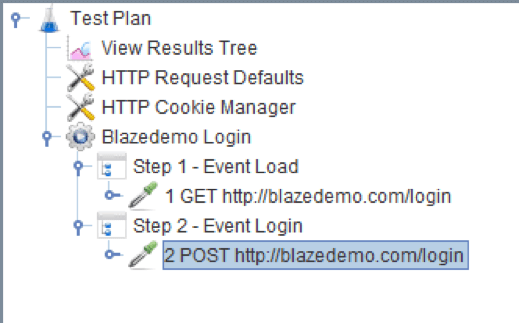
Let’s suppose that your script looks like this:
In Step 1 we go to the main login page and Step 2 we log into the page with a user and password (you can create your own account).
If we run this script we can see the same response that we have shown before, but in this case, from JMeter itself. Let’s look at the View Results Tree element. You can see the same XSRF token, with the same value:
So, what can we do if we need to set up a variable with the value of the XSRF-TOKEN? Here is where the JMeter Regular Expression Extractor comes to play.
Extracting the Token with the JMeter Regular Expression Extractor
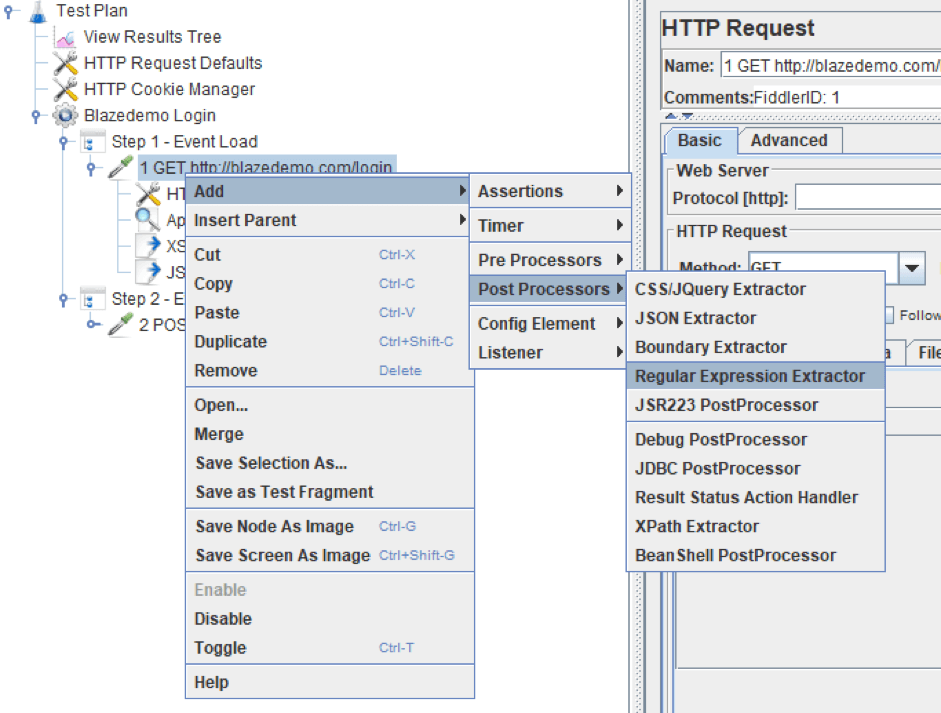
We need to extract the token from the answer. To do this we have to add a JMeter regular expression extractor to the request (right click over the request):
And set it as follows:
Selecting the options:
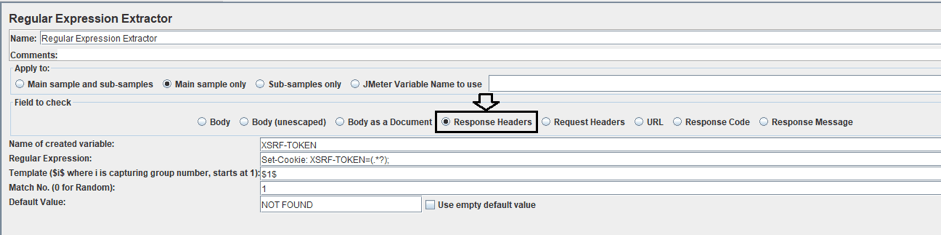
- Field to check: Response Header, because we want to extract a value that is given in the header of the response.
- Name of created variable: XSRF-TOKEN (you can choose the name you want).
- Regular Expression: Set-Cookie: XSRF-TOKEN=(.*?);
- Template: $1$ to indicate the group of the regular expression you want to save. In this case, we have only one group.
- Match No: 1. Number of match of the expression in the text we want to save.
- Default Value: NOT FOUND. Enter the test you want in the variable if the expression does not match. I choose NOT FOUND because it is easy for me to detect and see the sentence in the request and know easily if the expression is not matching.
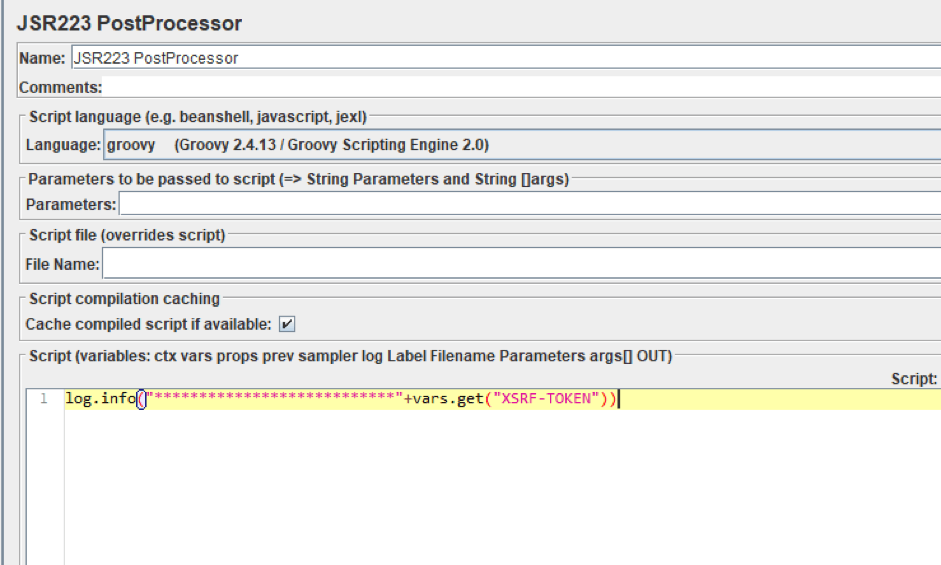
Let’s log the value that will be obtained by the regular expression after running the script, by adding a JSR223 PostProcessor:
log.info("***************************"+vars.get("XSRF-TOKEN"))
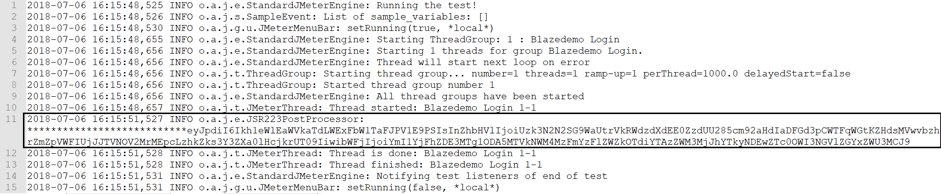
So, we can see the regular expression is working well and is saving the token in the variable defined:
2018-07-06 16:15:48,525 INFO o.a.j.e.StandardJMeterEngine: Running the test! 2018-07-06 16:15:48,526 INFO o.a.j.s.SampleEvent: List of sample_variables: [] 2018-07-06 16:15:48,530 INFO o.a.j.g.u.JMeterMenuBar: setRunning(true, *local*) 2018-07-06 16:15:48,655 INFO o.a.j.e.StandardJMeterEngine: Starting ThreadGroup: 1 : Blazedemo Login 2018-07-06 16:15:48,656 INFO o.a.j.e.StandardJMeterEngine: Starting 1 threads for group Blazedemo Login. 2018-07-06 16:15:48,656 INFO o.a.j.e.StandardJMeterEngine: Thread will start next loop on error 2018-07-06 16:15:48,656 INFO o.a.j.t.ThreadGroup: Starting thread group... number=1 threads=1 ramp-up=1 perThread=1000.0 delayedStart=false 2018-07-06 16:15:48,656 INFO o.a.j.t.ThreadGroup: Started thread group number 1 2018-07-06 16:15:48,656 INFO o.a.j.e.StandardJMeterEngine: All thread groups have been started 2018-07-06 16:15:48,657 INFO o.a.j.t.JMeterThread: Thread started: Blazedemo Login 1-1 2018-07-06 16:15:51,527 INFO o.a.j.e.JSR223PostProcessor: ***************************eyJpdiI6Ikh1eWlEaWVkaTdLWExFbW1TaFJPV1E9PSIsInZhbHVlIjoiUzk3N2N2SG9WaUtrVkRWdzdXdEE0ZzdUU285cm92aHdIaDFGd3pCWTFqWGtKZHdsMVwvbzhrZmZpVWFIUjJJTVNOV2MrMEpcLzhkZks3Y3ZXa0lHcjkrUT09IiwibWFjIjoiYmI1YjFhZDE3MTg1ODA5MTVkNWM4MzFmYzFlZWZkOTdiYTAzZWM3MjJhYTkyNDEwZTc0OWI3NGVlZGYxZWU3MCJ9 2018-07-06 16:15:51,528 INFO o.a.j.t.JMeterThread: Thread is done: Blazedemo Login 1-1 2018-07-06 16:15:51,528 INFO o.a.j.t.JMeterThread: Thread finished: Blazedemo Login 1-1 2018-07-06 16:15:51,531 INFO o.a.j.e.StandardJMeterEngine: Notifying test listeners of end of test 2018-07-06 16:15:51,531 INFO o.a.j.g.u.JMeterMenuBar: setRunning(false, *local*)
Now, you can work with the extracted variable in your script and use it in your requests (bodies and headers). You just have to invoke the variable as usual in JMeter, by typing ${XSRF-TOKEN}.
Extracting the Session ID
Now, suppose we also want to extract the laravel_session value. Well, the way to do it is the same.
Let’s add a new regular expression extractor:
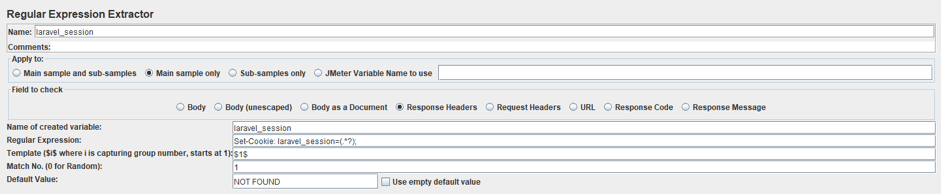
Selecting the options explained before:
- Field to check: Response Header.
- Name of created variable: laravel_session (you can choose the name you want).
- Regular Expression: Set-Cookie: laravel_session=(.*?);
- Template: $1$
- Match No: 1.
- Default Value: NOT FOUND.
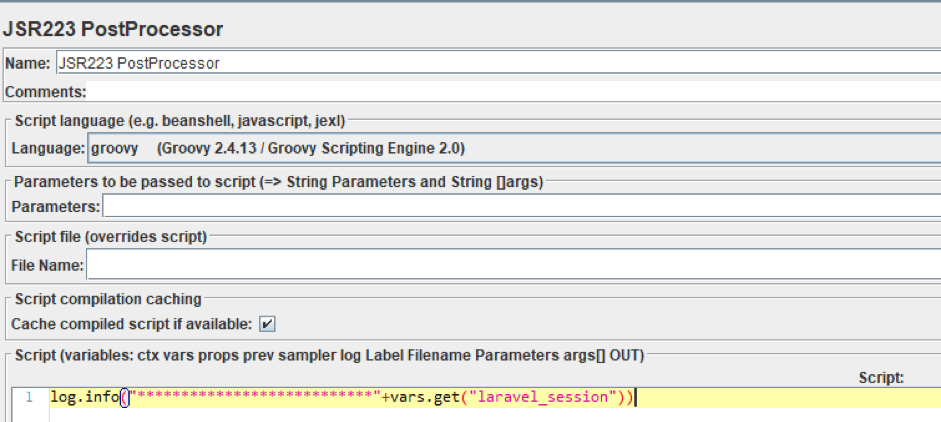
Now, log the value of the defined variable, as we have before:
log.info("***************************"+vars.get("laravel_session"))
You should see the value logged in the JMeter console:
2018-07-10 17:21:23,377 INFO o.a.j.e.JSR223PostProcessor: ***************************eyJpdiI6IitqUHVrR3FnUnJWcEhIbHlJM3ErOUE9PSIsInZhbHVlIjoiaE8wUk8rQ25DWnRwMWhmVFU3blRyWTZKeG9iVVhNT0hXRjltZkg0b1I1NFRZbm5IQ2RNRTVMU0JjYnVxaTE0UXhUbWtnb2cxTDFaOWt0UU5zYXM4NFE9PSIsIm1hYyI6IjVlNGY4NjViYzY4MzAwNTY1NjIwMTk4NjU1OWNkNWQ0OTcyZjQyZTMwMWNmNWQyMGQ5MmRlMDQ3OTY1N2Y3YmUifQ%3D%3D
Now, again, you just have to invoke the variable as is usual in JMeter, typing ${laravel_session}.
There are other options if the value you want to handle is a cookie. I hope working with these values will be a little easier for you now! Let us know in the comments.
Running Your JMeter Script in BlazeMeter
After creating your JMX file, you can massively scale your test by running it in BlazeMeter. By using BlazeMeter you will also be able to drill down into reporting, share tests and shift left.
Related Resources: